SSL is short for Secure Sockets Layer, and is a protocol originally designed by Netscape. TLS (Transport Layer Security) is the IETF version of SSL. Version 3.0 of SSL was used as the basis for the IETF TLS standard, version 1.0.
Using ECC for secure transactions makes sense for a number of reasons. Transactions will need to be processed more efficiently – more and smaller devices are being connected to the Internet that require security, from onboard automotive computers to smart cards and process control sensors. ECC uses less bandwidth than alternative cryptographic algorithms for SSL/TLS.
Processing power itself is increasing and hackers have even more resources available to them than ever before. Although 1024-bit RSA keys are currently most often used today, use of 2048 bits is becoming more and more common. The chart below shows the impact that this will have in server response time.

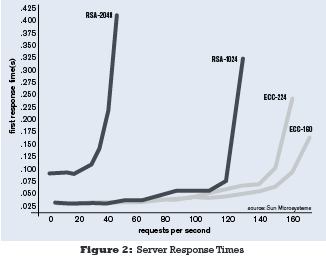
According to this chart, in order to handle the same amount of web traffic, someone using RSA instead of ECC would have to purchase and maintain 3.5 times as many web servers in order to handle the same amount of traffic.
Certicom, OpenSSL and Sun Microsystems are actively promoting the adoption of ECC into IETF standards, and have implemented ECC in TLS.
ECC Cipher Suites for TLS (draft-ietf-tls-ecc-06.txt) is the IETF draft thatdiscusses new key exchange algorithms based on ECC for the TLS (Transport Layer Security) protocol. In particular, it specifies the use of Elliptic Curve Diffie-Hellman (ECDH) key agreement in a TLS handshake and the use of Elliptic Curve Digital Signature Algorithm (ECDSA) as an authentication mechanism.
S/MIME can be used to secure email, allowing them to be encrypted, which protects them from being scanned and read. Furthermore, emails can be authenticated using S/MIME, which prevents modification of their contents and forgery of their originating address. This is commonly done in spam email, as well as in the more nefarious form called “Phishing”, where the sender spoofs the address of a legitimate authority, such as a bank or company IT department, in order to induce the recipient to reply with sensitive information.
RFC 3278 (Use of Elliptic Curve Cryptography (ECC) Algorithms in Cryptographic Message Syntax (CMS)) defines a profile for the use of ECC public key algorithms such as ECDSA, ECDH and MQV to secure email.
As with SSL, ECC uses less bandwidth and requires less computing power than alternative cryptographic algorithms for S/MIME, which can be critical for devices like PDAs and smartphones, which are beginning to support email. In addition, many of the security benefits of MQV that have been highlighted in previous issues of Code and Cipher will apply when MQV is used in S/MIME. In the context of email, using MQV in S/MIME allows a sender to authenticate email to a recipient rather the sender digitally signing the email for anybody to see.
Currently, deployment of S/MIME is still in its early days. As S/MIME adoption increases, use of ECC-based algorithms within S/MIME should also increase.
RFC 3279 (Algorithms and Identifiers for the Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile)describes the encoding formats for the digital signatures and public keys for ECDSA and ECDH.
This RFC is important not only to PKIX, but also to IPSec, SSL/TLS and S/MIME as well because it describes the certificates that are used for all of these Internet protocols.
There are many other Internet drafts and standards that include ECC:
There are a number of ongoing efforts to have ECC incorporated into IETF standards. Moreover, companies are already using ECC-based algorithms today in their Internet communications. Elliptic Curve Cryptography is emerging as the best option where performance is a concern, and as such, it is important to ensure that it continues to be written into drafts and adopted as RFCs.
The IETF: www.ietf.org
PSec RFC: http://www.faqs.org/rfcs/rfc2409.html
SMIME RFC: http://www.faqs.org/rfcs/rfc3278.html
PKIX RFC: http://www.faqs.org/rfcs/rfc3279.html
ECC Cipher Suites for TLS (draft-ietf-tls-ecc-06.txt) ftp://ftp.rfc-editor.org/in-notes/internet-drafts/draft-ietf-tls-ecc-06.txt
ECC is included in numerous standards around the world. This issue of Code and Cipher focuses on three key standards bodies that incorporate ECC: ANSI, IETF and NIST.