As has been demonstrated in past issues of Code and Cipher, ECC is the best option for public-key cryptography when performance is a concern. One area where good performance is important is Internet communication.
The body that looks after setting the standards for Internet communication protocols is the Internet Engineering Task Force (IETF). IETF has been very influential in the cryptographic standards industry by setting the widely used standards for IPSec, TLS and S/MIME.
ECC provides performance benefits for Internet communications, and indeed companies are using ECC today within these protocols. This article summarizes some of the main areas where ECC is being used for Internet communications.
The IETF is a large, open and international community of software and network designers, operators, vendors, and researchers concerned with the evolution of the Internet architecture and the smooth operation of the Internet. The IETF holds meetings three times a year, and anyone can attend. The rest of the time participants communicate via mailing lists.
The actual technical work of the IETF is done in its working groups, which are organized by topic into eight different areas. Security is one of these groups.
IETF standards begin as Internet Drafts (I-D). To become an IETF standard, the document must be published as an I-D so that interested participants can provide comments and feedback. After a period of time, the draft is presented to the IESG (Internet Engineering Steering Group) for review and publishing, and is assigned an RFC (Request for Comments) number by the RFC Editor.
Elliptic Curve Cryptography can be found in RFCs and I-Ds for all the key Internet protocols: IPSec, TLS, PKIX, and S/MIME.
IPSec is one of the protocols where ECC is in use today. Typically, IPSec uses DH (Diffie Hellman) for key generation, which is fine for a desktop connection, but is too slow for smaller devices (see Figure 1). ECDH (Elliptic Curve Diffie Hellman) provides much faster performance. As more companies want to enable secure connections from constrained devices such as smart phones and handhelds, connection time becomes an important consideration.
Figure 1. Relative key set up times (IKE)
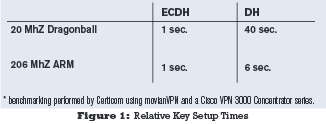
* benchmarking performed by Certicom using movianVPN and a Cisco VPN 3000 Concentrator series.
Cisco, Shiva and Nortel all support ECDH for key exchange in their gateways. RFC 2409 (The Internet Key Exchange (IKE)) describes the use of certain ECC curves for IKE. Cisco, Shiva and Nortel actually base their IKE implementations of ECDH on Internet Drafts that describe stronger ECC curves. They are using Additional ECC Groups for IKE ( draft-ietf-ipsec-ike-ecc-groups-04.txt), which describes how to use some NIST-recommended curves with IKE.
This issue of Code & Cipher reviews the first annual Certicom ECC Conference and summarizes some of the key discussions at the event.