A secure protocol should be able to withstand both passive attacks and active attacks. In a passive attack, an adversary attempts to prevent a protocol from achieving its goals by merely observing honest entities carrying out a protocol. In an active attack, an adversary subverts the communications by injecting, deleting, altering or replaying messages.
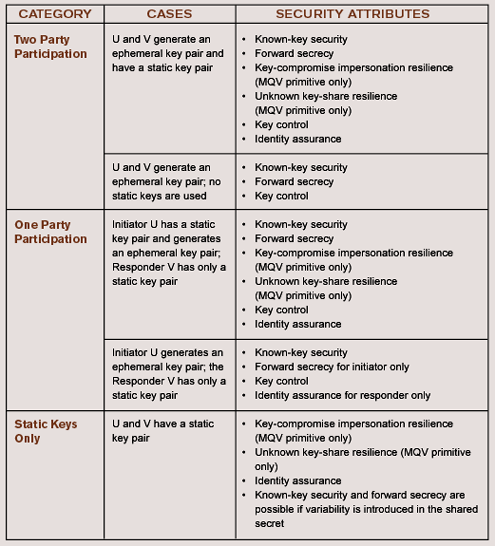
The following are the primary security attributes that key establishment schemes can possess (explained by way of example between entities U and V):
In addition to these security attributes, key establishment schemes can be compared by their performance attributes, such as a minimal number of passes, low communication overhead and low computation overhead. These performance attributes are extremely important for constrained devices such as smart phones, PDAs and other wireless devices with limited resources.
In some cases, the key establishment scheme will be chosen as part of the security protocol being implemented. In other cases, you need to carefully weigh the different options and choose based on which security attributes are most desirable. The main consideration then is the primitive, either DH or the MQV algorithm, selected for key establishment and how it’s computed, DLC over finite fields or ECC.
The bottom line is that you need to carefully consider key establishment schemes whenever you are designing a protocol or implementing a security system. As this article shows, there are many different key establishment schemes endorsed by the standards. So your choice comes down to carefully weighing the tradeoffs between the different security attributes and the performance attributes. Generally, key establishment using ECC and MQV yield the best results in terms of the security performance tradeoff.
This issue of Code & Cipher reviews the first annual Certicom ECC Conference and summarizes some of the key discussions at the event.