Many systems need to use well-established cryptography to protect the integrity and confidentiality of the data. Symmetric algorithms such as the 128-bit Advanced Encryption Standard (AES) provide strong protection beyond the year 2036. However, the use of AES requires the establishment of shared keying material in advance.
While a courier could be used to manually distribute the keying material, this is not practical when the number of people using a system grows because the distribution work grows quadratically. Therefore, it’s essential to support symmetric algorithms with key agreement schemes.
Key agreement is a technique for parties who wish to engage in secure communications in which both parties contribute to the establishment of a shared secret. The shared secret is used to derive a symmetric key, which in turn is used to establish a secure channel. The method by which the shared secret is generated is known as key agreement and it is useful for applications in which parties are exchanging data in real time. A critical requirement for key agreement is the assurance that eavesdroppers are unable to obtain the shared secret.
The article on Key Establishment Schemes (found in this issue of Code and Cipher) outlines a number of different options for key establishment and the desirable security attributes. This article focuses on two schemes for key agreement: the Elliptic Curve Diffie-Hellman (ECDH) and Elliptic Curve Menezes-Qu-Vanstone (MQV).
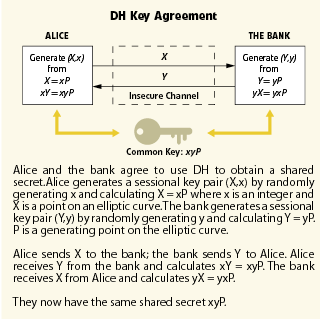
ECDH is the elliptic curve analog of the traditional Diffie-Hellman key agreement algorithm. The Diffie-Hellman method requires no prior contact between the two parties. Each party generates a dynamic, or ephemeral, public key and private key. They exchange these public keys. Each party then combines its private key with the other party’s public key to form the shared secret. This method is also known as carrying out an ECDH key agreement.
An example of ECDH key agreement is a home-banking subscriber, Alice, setting up a secure communication channel with her bank. Alice generates a public key and a private key; she sends the public key to her bank. Independently, her bank generates a public key and a private key; the bank’s public key is sent to Alice. Alice combines her private key and the bank’s public key to form a shared secret. Her bank combines its private key and Alice’s public key to arrive at the same shared secret. The shared secret may now be used to generate a key for encrypting and decrypting the communication session. Figure 1 illustrates the use of DH for this session.
The problem with DH is that Alice may be setting up a secure session with someone impersonating her bank. Because the private and public keys are generated on the fly, there is no way to prove you have a secure session with the intended party unless you add a method for user authentication. MQV addresses this issue.
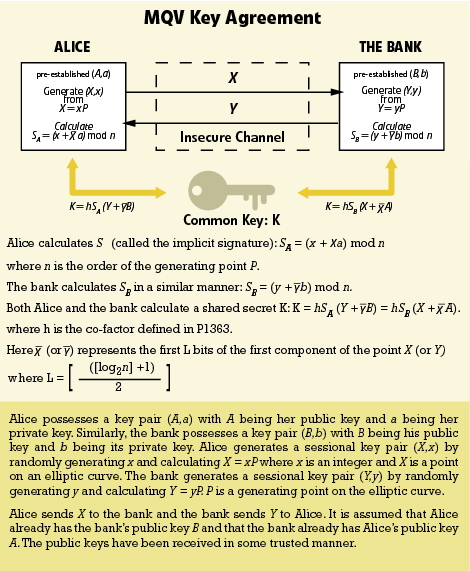
The MQV elliptic curve key agreement method is used to establish a shared secret between parties who already possess trusted copies of each other’s static public keys. Both parties still generate dynamic public and private keys and then exchange public keys. However, upon receipt of the other party’s public key, each party calculates a quantity called an implicit signature using its own private key and the other party’s public key. The shared secret is then generated from the implicit signature. The term implicit signature is used to indicate that the shared secrets do not agree if the other party’s public key is not employed, thus giving implicit verification that the public secret is generated by the public party. An attempt at interception will fail as the shared secrets will not be the same shared secrets because the adversary’s private key is not linked to the trusted public key.
To return to the example of Alice communicating with her bank. If Alice has the bank’s public key and the bank has Alice’s public key then the MQV key exchange may be used. Anyone intercepting the transmissions and substituting the public key is unable to communicate because the resulting shared secrets differ.
While based on DH, MQV offers attributes – such as key-compromise impersonation resilience and unknown key-share resilience – that are not found with DH. This allows protocols that use MQV for key agreement to offer stronger authentication and ensure malicious entities cannot masquerade as a third party to the entity whose key was compromised.
MQV also has many desirable performance attributes, including the fact that the dominant computational steps are not intensive while the protocol also has low communication overhead, is role-symmetric, non-interactive and does not use encryption or time-stamping.
The result is that MQV has all the desirable security attributes of key establishment as outlined in the article on Key Establishment Schemes and if computed using Elliptic Curve Cryptography offers significant performance advantages over other key establishment schemes. This makes it ideal in the development of security protocols and systems that require efficient and authenticated key agreement.
This issue of Code and Cipher focusses on the subject of key establishment in current security standards and highlights the importance of this often overlooked but central area of concern.