ECC stands for Elliptic Curve Cryptography. It represents a different way to do public-key cryptography—an alternative to the older RSA system—and also offers certain advantages.
ECC devices require less storage, less power, less memory, and less bandwidth than other systems. This allows you to implement cryptography in platforms that are constrained, such as wireless devices, handheld computers, smart cards, and thin-clients. It also provides a big win in situations where efficiency is important.
For example, the current key-size recommendation for legacy public schemes is 2048 bits. A vastly smaller 224-bit ECC key offers the same level of security. This advantage only increases with security level—for example, a 3072 bit legacy key and a 256 bit ECC key are equivalent—something that will be important as stronger security systems become mandated and devices get smaller.
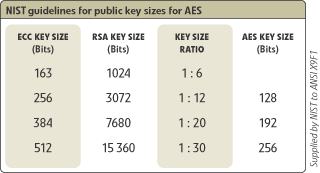
NIST, ANSI and IEEE have standardized ECC, as detailed below.
The National Institute of Standards and Technology (NIST) issues standards that mandate what cryptographic algorithms US Federal Government agencies can use, such as:
The American National Standards Institute (ANSI) committee X9 develops standards for the US financial services industry, including:
The Institute for Electrical and Electronics Engineers (IEEE) develops standards, including the following:
IEEE 1363-2000: Standard Specifications for Public Key Cryptography. This specifies ECDSA, ECDH, and ECMQV.
Other bodies recommending ECC are Europe's NESSIE and Japan's CryptRec and ISO globally.
Applications of ECC have also been standardized by IETF and other organizations, including PKIX.
Yes.
MQV is short for Menezes-Qu-Vanstone, the names of the authors of this protocol. It is a method of key agreement, which is related to Diffie-Hellman, but offers some significant advantages.
MQV offers attributes—such as key-compromise impersonation resilience and unknown key-share resilience—that are not found with DH. This allows protocols that use MQV for key agreement to offer stronger authentication and ensure malicious entities cannot masquerade as a third party to the entity whose key was compromised.
MQV also has many desirable performance attributes, including the fact that the dominant computational steps are not intensive while the protocol also has low communication overhead, is role-symmetric, non-interactive and does not use encryption or time-stamping.
The MQV protocol was the focus of the second issue of Code and Cipher, Certicom's quarterly newsletter on the security industry. Additionally, a paper describing MQV entitled "An Efficient Protocol for Authenticated Key Agreement", can be found at: http://www.cacr.math.uwaterloo.ca/techreports/1998/corr98-05.pdf