Securing VoIP networks today is about more than securing the signaling and media channels – it is also about securing the VoIP device itself.
As more and more connected devices are deployed, it is becoming increasingly important to have the ability to remotely provision and configure those devices, and to remotely update software in devices deployed throughout the network. These software updates need to be protected, not just while in transit but also to ensure that the update received by the device came from a reliable source, and is free from malicious elements.
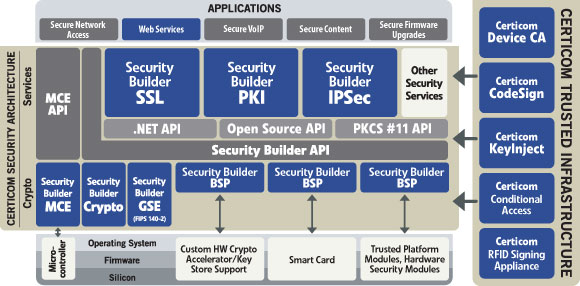
To achieve strong and comprehensive VoIP security, security needs to be designed into the device to authenticate the VoIP device itself, and the underlying software, including the boot code, operating system, drivers, and applications.
Certicom Security for VoIP provides developers with the tools they need to quickly and cost-effectively add strong security to their VoIP devices. The solution includes the Certicom® Security Architecture™ and Certicom® CodeSign™, with the following components: