Increased network use to communicate sensitive data and complete critical transactions has created a need for greater confidence in the identities of the person, computer, or services involved in the communication. Digital certificates and public-key cryptography provide an enhanced level of authentication and privacy to digital communications that cannot be achieved by passwords alone.
There are three key types of algorithms that are used for digital certificates: RSA, DSA and ECDSA (Elliptic Curve Digital Signature Algorithm). Other signature algorithms include ECPVS (Elliptic Curve Pintsov Vanstone Signatures), which provides partial message recovery, ECQV (Elliptic Curve Qu Vanstone): an implicit certificate type and ECNR (Elliptic Curve Nyberg Rueppel): which provides full message recovery.
To date, RSA and DSA have enjoyed wide use in applications ranging from anti-cloning to secure firmware updates. However, changing security and performance requirements, as well as the shift to smaller, more mobile devices, are pointing towards a need for smaller and faster signatures. Moreover, the National Security Agency (NSA) requires that signatures used today last for the next 50 years. These requirements pave the way for digital certificates that use Elliptic Curve Cryptography (ECC)-based signatures.
Using ECC-based signatures with digital certificates provides added size and performance advantages. This article provides an overview of what certificates are and examines how digital certificates are used in applications—applications that have wider adoption possibilities beyond the markets outlined here.

Digital certificates are electronic credentials that are used to verify the identities of individuals and devices. They have one primary function: to attest that the ID data is bound to the public key. Like any physical identification, they can be created, expired, renewed, revoked or suspended. Digital certificates are typically issued by recognized organizations that can verify the certificate requestor’s identity—a business, a government agency, or a bank. This ensures that once the certificate is issued, the identity of the requestor can be trusted by all who trust the authority.
Digital certificates are made up of three parts. The first part of a certificate is the identification information for the user or device. Second is a public key, associated with a private key that is kept by the user. The third part of the digital certificate is the digital signature.
The advantages of ECC-based certificates are two-sided:
ECC-based signatures on a certificate are smaller and faster to create; and the public key that the certificate holds is smaller and more agile as well. Verification is also faster using ECC-based certificates, especially at higher key strengths. The reason can be found in the basic math behind elliptic curves. As highlighted in other issues of Code and Cipher, the security of ECC systems is based on the elliptic curve discrete logarithm problem, rather than the integer factorization problem. This difference allows ECC systems to start out smaller, and scale more efficiently as the bit size of the matching symmetric key increases. Ultimately, this allows for faster computations and smaller key sizes for comparable security.
Table 1 demonstrates the performance of ECDSA over RSA for signing and verifying. The ECC and RSA signatures compared at each level are of equivalent strength, despite the difference in signature size. The chart measures the number of digital signatures applied to a data block per minute.
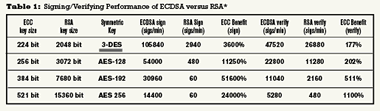
At all levels, which are NIST (National Institute of Standards in Technology) recommended key sizes, using ECDSA provides incredible performance benefits to both signing and verification operations. The benefits of ECC-based digital certificates become even more apparent when applied to some of today’s applications.
The Check Clearing Act for the 21st Century (Check 21) allows financial institutions to securely exchange image replacement documents, eliminating the paper trail associated with clearing checks and reducing overall operation and administrative costs. A more complete discussion of Check 21 can be found in Code and Ciphervolume 1, issue 3.
Check 21 poses a security risk if images are altered at any point in the check exchange process. Digital certificates can mitigate this risk.
Each bank obtains its own certificate, which contains the corresponding public/private key pair. The private key generated during the certificate request process is securely stored and encrypted within the banks’ trusted database. This private key is used to generate the signature of an image. The signature and the certificate containing the certified public key are appended to the corresponding check image. This protects the image from tampering and fraud as it progresses through the payment system.
RSA, DSA, and ECDSA are all approved as signature methods in ANSI X9.37.** Because of its relative small size, however, ECDSA provides greater efficiency and performance (especially at higher security levels). The size of ECDSA signatures also benefits the archiving process. An image captured today would need to be archived until 2012. To ensure adequate security, a 2048-bit RSA or equivalent 224-bit ECDSA signature would need to be applied. The smaller ECDSA signatures minimize overall footprint on each image, resulting in cost savings for storage.
This issue of Code and Cipher examines different types of certificates, their uses and benefits.